During these days we're hearing about #Shellshock bug, and I's just wondering if the Sysadmin of US DoD network is going to invite everybody to the big party with all these attacks,botnets, forkbombs,etc :P stay alert ,During all these two days one of the major flaws has been exploited and that's the obviously! , Who does not like free shells :3, there're right now tons of people creating new PoC's now imagine how money could you get :P Do you imagine how the defense should be.
I've been collecting a couple of fun pics regarding to this topic , enjoy it .
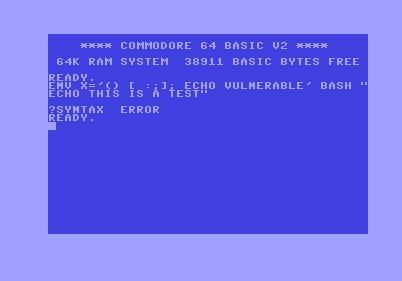
Fig.1 I can't reproduce #shellshock on this system either! Plz help.
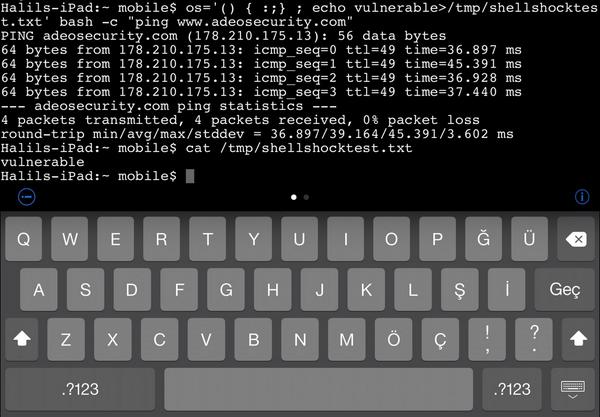
Fig.2 Jailbreaked iOS 7.1.2 #shellshock test result.
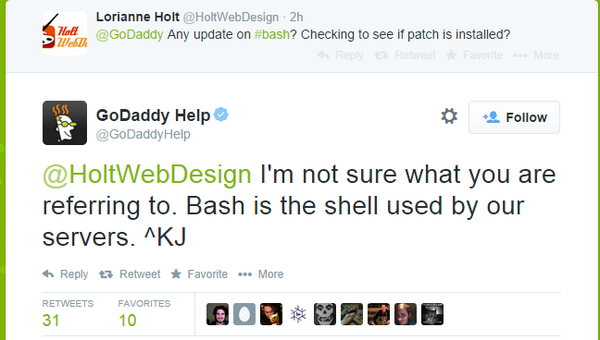
Fig.3 For a laugh: *Facepalm* Oh GoDaddy... #Shellshock #CVE20146271 #bashbug #bashbleed #bashpocalypse #infosec

Fig.4 #infosec #shellshock #bashbleed #bashpocalypse
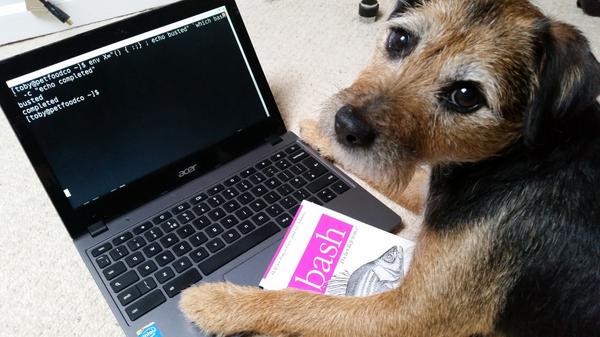
Fig.5 Lol In your servers, stealing your secretz #bashbug #shellshock
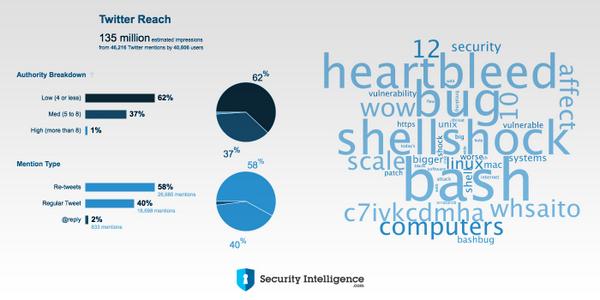
Fig.6 How many people already talking about #shellshock? About 40K tweets by 46K users since yesterday. #bash #bashbug

Fig.7 Since 90's ?

Fig.8 In the Wake of Shellshock, Mac Users Are Left Waiting for a Patch via @mashable http://avgclick.me/1n46EUP

#Shellshock: All you need to know about the #BashBug vulnerability http://symc.ly/1u21HMX



