The FBI filled in some blanks Friday by noting that "technical analysis of the data-deletion malware used in this attack revealed links to other malware that the FBI knows North Korean actors previously developed," including "similarities in specific lines of code, encryption algorithms, data deletion methods, and compromised networks." The FBI also found Internet addresses linked to North Korea in the malware involved in the attack
12/21/2014 Sony 'made a mistake'???
9/26/2014 #Shellshock Images of the Week
During these days we're hearing about #Shellshock bug, and I's just wondering if the Sysadmin of US DoD network is going to invite everybody to the big party with all these attacks,botnets, forkbombs,etc :P stay alert ,During all these two days one of the major flaws has been exploited and that's the obviously! , Who does not like free shells :3, there're right now tons of people creating new PoC's now imagine how money could you get :P Do you imagine how the defense should be.
I've been collecting a couple of fun pics regarding to this topic , enjoy it .
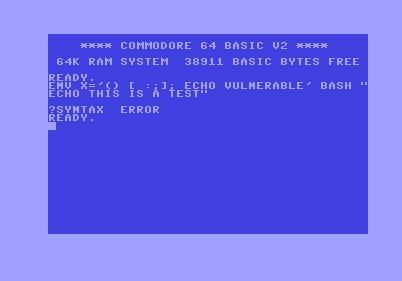
Fig.1 I can't reproduce #shellshock on this system either! Plz help.
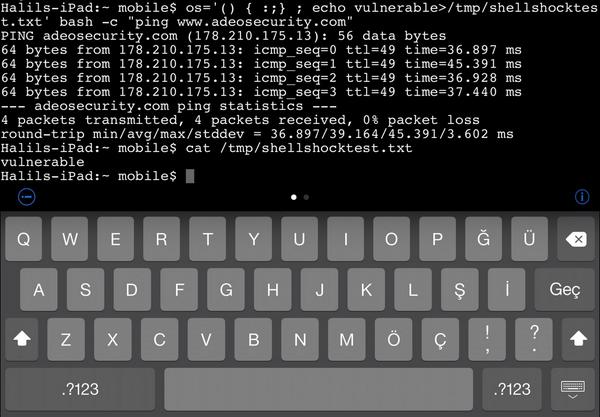
Fig.2 Jailbreaked iOS 7.1.2 #shellshock test result.
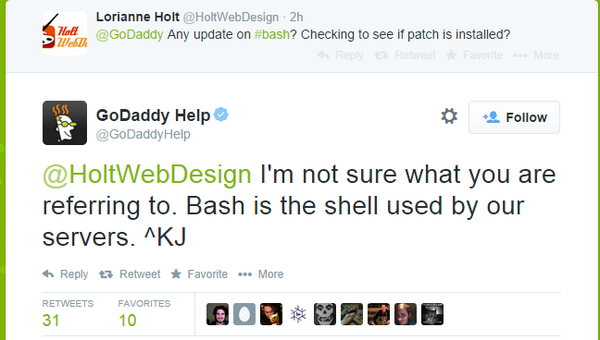
Fig.3 For a laugh: *Facepalm* Oh GoDaddy... #Shellshock #CVE20146271 #bashbug #bashbleed #bashpocalypse #infosec

Fig.4 #infosec #shellshock #bashbleed #bashpocalypse
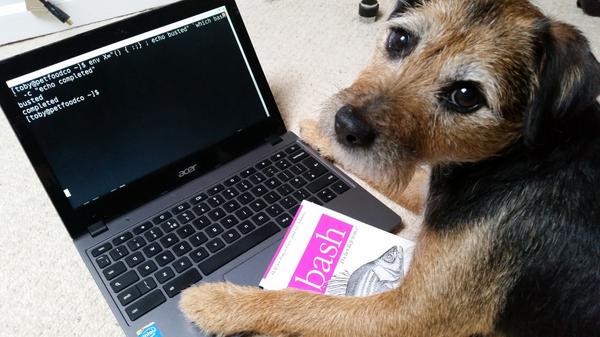
Fig.5 Lol In your servers, stealing your secretz #bashbug #shellshock
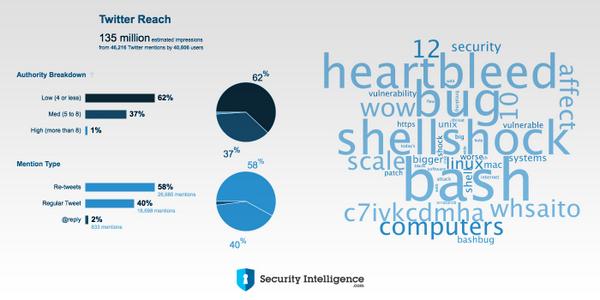
Fig.6 How many people already talking about #shellshock? About 40K tweets by 46K users since yesterday. #bash #bashbug

Fig.7 Since 90's ?

Fig.8 In the Wake of Shellshock, Mac Users Are Left Waiting for a Patch via @mashable http://avgclick.me/1n46EUP

#Shellshock: All you need to know about the #BashBug vulnerability http://symc.ly/1u21HMX

9/01/2014 Pwnables.kr
Well this post is to share with you an amazing site saw in #pwning channel ,I say that because in this site we can practice all the important aspects (Reversing, Programming, System Knowledge and Exploitation)it has a special thing where you need to know about Gnu/Linux Operative System and it is intended for students,professionals and enthusiast of Information Security.
The site is divided in four categories as it is explained below :
|
Play Just for fun not for profit.
Etiquetas:
challenges,
ctf,
Unix,
wargame
4/20/2014 April 22nd is Earth day
This year I'm working with a near partner in my university as you maybe know in april 22 is Earth day an special day for our planet.We're going to plant new trees if you want to join please leave me a message using the contact box or reachme in twitter.
Plant trees plant life Pick a tree that you know can survive in your climate. If you're unsure about what that might be, ask an employee at your local garden shop, or inside the garden department of a big-box store.
Learn more about the environment. Earth Day is a good time to make a commitment to learning more about the environment and how you can help to protect it. Borrow some library books and read up on an issue such as pollution, endangered species, water shortages, recycling, and climate change. Or, learn about a region you've never considered before, like the Arctic, the deserts, or the rain forests. Think about the issues that concern you the most and if you haven't done so already, join a local group that undertakes activities to help protect the environment in your area.
Where:
Universidad Tecnologica de Pereira
When :
April 22 , at 9 a.m Electrical Building.
Plant trees plant life Pick a tree that you know can survive in your climate. If you're unsure about what that might be, ask an employee at your local garden shop, or inside the garden department of a big-box store.
Learn more about the environment. Earth Day is a good time to make a commitment to learning more about the environment and how you can help to protect it. Borrow some library books and read up on an issue such as pollution, endangered species, water shortages, recycling, and climate change. Or, learn about a region you've never considered before, like the Arctic, the deserts, or the rain forests. Think about the issues that concern you the most and if you haven't done so already, join a local group that undertakes activities to help protect the environment in your area.
Where:
Universidad Tecnologica de Pereira
When :
April 22 , at 9 a.m Electrical Building.
4/06/2014 Weekly Security Reactions
When I submit a bug report, but someone else already got the bounty.
It seems like a local situation :3
It seems like a local situation :3
4/04/2014 The Fall of Hacker Groups
As we know during decades there were legendary hacking groups , This article posted by strauss in phrack magazine in april 4 is really nice and you must read here http://phrack.org/papers/fall_of_groups.html.
Just take a moment , and think on this wise words of wisdom.
Hacking is, in its very essence, an underground movement. Those who take part on it have always been the ones who (ab)used technology in ways beyond the knowledge of the larger userbase. It is tightly linked to intense efforts in unveiling previously unknown information as well as in sharing these discoveries. These premises hold true for as long as we know hackers: since computers had barely no users up until the informatic massification of today. The nature of the hacker interests intrinsically poses difficulties: growing knowledge on anything is hard. It requires heavy research, experimentation, and can turn into an endless journey if objectives are not carefully set. Just like in any field of scientific studies, it calls for a good amount of colaboration, an attitude which, luckily for hackers, was greatly enabled by the advent of computer networks and, most notably, the Internet. Computer networks increasingly made it possible to transmit unlimited and uncensored information across their geographical extent with little effort, with little costs, and in virtually no time. From the communication development standpoint, one would expect that the events that followed the 80s to our days would lead to a geometric progression in the number of hacker communities. In effect, hacking has arguably grown. Hacker communities, definitely not.
Just take a moment , and think on this wise words of wisdom.
2/17/2014 Olympic CTF 2014 - Binathlon (400)
2/15/2014 Analisis de Circuitos Teoria y Practica
Hace algún tiempo estuve buscando este libro en pdf pero por desgracia no lo encontré.
La primera vez que vi este libro fue en la biblioteca de la universidad cuando recién comenzaba a crear mis primeros proyectos de electrónica, hoy lo encuentro así que lo dejare aquí para mi y por si alguien que lea este blog lo quiere aquí esta.
Link de Descarga:
https://mega.co.nz/#!R5kwWbxI!269ikcaGAb-l7Esd6nrCFft3uK5RQ-6MHCWxfNycKvE
https://drive.google.com/file/d/0B9KYv-mwSafXbVFaZGVUM0dUUjA
https://drive.google.com/file/d/0B9KYv-mwSafXbVFaZGVUM0dUUjA
Etiquetas:
circuits and electronics,
electronica
2/05/2014 Rate My Network Diagram!
If you have been searching on the web for network diagrams of large,small and home networks this site is for you.
Link : http://www.ratemynetworkdiagram.com/
Here you will be able to rate the network from 0(worst) to 10 (awesome!), this vote will be added to the rating system within this awesome site.It is recommended for ccna students , pentesters and so on.
The idea of setting this site up was not to make it possible for people to vote on the "look" of a network diagram. The purpose of this site is to allow people to learn about computer networking and network documentation by seeing what other people have done with their networks -- all for free.
Along with rating network diagrams, users may also leave comments or messages in the RMND forum to interact with other users of the site. When rating other user's network diagrams or designing your own diagram, please keep in mind ratings should be based on the function of the network and not the graphic design capabilities of the network administrator.
How it works: You signup and become a member. Once signed up you can upload your image. Once we approve your image, it will begin to appear on the site. Visitors will view your image and rate it depending on their own personal opinion of the flow, functionality, implementation, etc. of your network. Visitors may also leave public comments about you, and some may even decide to leave you a private message.
Rules: No porn allowed! We approve all images before being shown on the site. So you lose either way, if you upload porn you will be deleted. To keep the site as fast as possible, all images must be smaller than 350 Kb in file size.
Link : http://www.ratemynetworkdiagram.com/
2/04/2014 Steve Irwin Tribute by Melodysheep
I just found this on my twitter timeline :
Awesome :P Not , there is nothing more in the world that you being happy and this man was really happy with cocodriles and I Appreciate this things ...Passion
Melodysheep shares the world of wildlife through the words and life of Steve Irwin in this new remix: http://t.co/P0aj454ulD @musicalscience
— Machinima (@Machinima) February 5, 2014
Awesome :P Not , there is nothing more in the world that you being happy and this man was really happy with cocodriles and I Appreciate this things ...Passion
1/25/2014 Fuses for Pic18f4550
Microcontrollers are really awesome , they are everywhere that's the reason why actually I'm working on a proyect that involves it. The market has a wide range of manufacturers like Atmel, Microchip, Motorola among others in order to this I've chosen Microchip by his usability and his features between them :
memories(ROM , RAM, EEPROM), Ports, serial IO (input and output) devices, Timers and Interrupt sources, Adc converters, Comparator, Pwm modules and others.
Another thing to say is they are commonly know as PIC microcontrollers PIC or just PICmicro. They have a Harvard architecture, and instruction words are unusual sizes. Originally, 12-bit instructions included 5 address bits to specify the memory operand, and 9-bit branch destinations. Later revisions added opcode bits, allowing additional address bits.
Picmicro are divided in family based on the word assembly language instruction, varying from 8 ,16, 32 bits depending on the specific PIC.The family clasification can be found here :
http://www.microchip.com/pagehandler/en-us/products/picmicrocontrollers
When you're in a proyect you need to make the right choices and this pic is great it came with 32Kb of flash memory and other nice features, here is a sumary of the most valuable:
Fuses Pic 18f4550:
As we can read in the quote above they're necesary for a proper operation , the other thing is that when you're flashing out this chips they have a code protection fuses which if you activate this you won't be able to use the microcontroller again,because you're protecting a session in rom memory.
Here are the fuses that I've been using this week, remember this is for a pickit 3 proper development , this will work with another programmer that has circuit debuger like icd and others.
just save this code as a fuses.h and include in your main.c program.
memories(ROM , RAM, EEPROM), Ports, serial IO (input and output) devices, Timers and Interrupt sources, Adc converters, Comparator, Pwm modules and others.
Another thing to say is they are commonly know as PIC microcontrollers PIC or just PICmicro. They have a Harvard architecture, and instruction words are unusual sizes. Originally, 12-bit instructions included 5 address bits to specify the memory operand, and 9-bit branch destinations. Later revisions added opcode bits, allowing additional address bits.
Picmicro are divided in family based on the word assembly language instruction, varying from 8 ,16, 32 bits depending on the specific PIC.The family clasification can be found here :
http://www.microchip.com/pagehandler/en-us/products/picmicrocontrollers
Pic 18f4550:
| Pic 18f4550 |
- IC, 8BIT FLASH MCU, 18F4550, PDIP40
- Controller Family/Series: PIC18F4xxx
- Program Memory Size: 32KB
- RAM Memory Size: 2KB
- CPU Speed: 48MHz
- No. of I/O's: 35
- Digital IC Case Style: DIP
- No. of Pins: 40
- Embedded Interface Type: EUSART, I2C, SPI, SPP, USB
- Supply Voltage Min: 4.2V
- Supply Voltage Max: 5.5V
- MSL: -
- SVHC: No SVHC (20-Jun-2013)
- Core Size: 8bit
- Device Marking: PIC18F4550-I/P
- EEPROM Memory Size: 256Byte
- Flash Memory Size: 32KB
- IC Generic Number: 18F4550
- IC Temperature Range: Industrial
- Logic Function Number: 18F4550
- Memory Type: Flash
- Microprocessor/Controller Features: SPI, I²C, CCP, ECCP, SPP, EUSART, 2 x Comparators, 1 x 8-bit timer, 3 x 16-bit timer
- No. of ADC Inputs: 13
- No. of Bits: 8
- No. of Internal Interrupts: 20
- No. of PWM Channels: 5
- No. of Timers: 4
- Number of bits In Timer: 16
- Number of bits in ADC: 10
- Operating Temperature Max: 85°C
- Operating Temperature Min: -40°C
- Operating Temperature Range: -40°C to +85°C
- Oscillator Type: External, Internal
- Peripherals: ADC, Comparator, PWM, Timer
Fuses Pic 18f4550:
This part was taken from the avr tutorials its very well explained:
Fuses are an extremely important part programming a chip, but are rarely explained thoroughly. You only need to set them once, but if you don't do it right, it's a disaster!
What is a fuse?
You know about flash, eeprom and RAM as parts of the chip. What I did not mention is that there are also 3 bytes of permanent (by permanent I mean that they stick around after power goes out, but that you can change them as many times as you'd like) storage called the fuses. The fuses determine how the chip will act, whether it has a bootloader, what speed and voltage it likes to run at, etc. Note that despite being called 'fuses' they are re-settable and dont have anything to do with protection from overpowering (like the fuses in a home).
As we can read in the quote above they're necesary for a proper operation , the other thing is that when you're flashing out this chips they have a code protection fuses which if you activate this you won't be able to use the microcontroller again,because you're protecting a session in rom memory.
Here are the fuses that I've been using this week, remember this is for a pickit 3 proper development , this will work with another programmer that has circuit debuger like icd and others.
just save this code as a fuses.h and include in your main.c program.
#ifndef FUSES_H
#define FUSES_H
#ifdef __cplusplus
extern "C" {
#endif
//******************************************
//FUSES USADOS CON CRISTAL DE 20MHZ Y USO DE PROGRAMADOR PICKIT3,
#pragma config PLLDIV = 5 // (CRISTAL DE 20 MHz),Divide by 5 (20 MHz oscillator input)
#pragma config USBDIV = 2 //USB clock source comes from the 96 MHz PLL divided by 2
#pragma config CPUDIV=OSC1_PLL2 //Primary Oscillator Src/1][96 MHz PLL Src/2] cpu trabajara a 48Mhz.
#pragma config FOSC = HSPLL_HS //HS oscillator, PLL enabled (HSPLL)
#pragma config FCMEN = OFF //Fail-Safe Clock Monitor disabled
#pragma config IESO = OFF //Oscillator Switchover mode disabled
#pragma config PWRT = ON //Power-up Timer Enable bit
#pragma config BOR = OFF //Brown-out Reset Enable bits: Brown-out Reset
//enabled in hardware only (SBOREN is disabled)
#pragma config BORV = 0 //Brown-out Reset Voltage bits,Maximum.
#pragma config VREGEN = ON // USB voltage regulator enabled
#pragma config WDT = OFF //WDT disabled (control is placed on the SWDTEN bit)
#pragma config WDTPS = 32768 //Watchdog Timer Postscale Select bits>> 1:32768
#pragma config MCLRE = ON //MCLR pin enabled; RE3 input pin disabled
#pragma config LPT1OSC = OFF //Timer1 configured for higher power operation
#pragma config PBADEN = OFF //PORTB<4:0> pins are configured as digital I/O on Reset
//If i need to use the RBx as analog in/out set this bit to ON
#pragma config STVREN = OFF //Stack full/underflow will not cause Reset
#pragma config LVP = OFF //PROGRAMACION EN BAJO VOLTAJE
#pragma config XINST = OFF // Instruction set extension and Indexed Addressing mode enabled
//the above bit is used enterely for debug program in circuit (ICPORT)
#pragma config CP0 = OFF //Code Protection bit disable for 0,1,2
#pragma config CP1 = OFF //
#pragma config CP2 = OFF //
#pragma config CPB = OFF //Boot Block Code Protection bit:
#pragma config CPD = OFF //Data EEPROM Code Protection bit.
#pragma config WRT0 = OFF //Write Protection bit for 0,1,2 is not write-protected
#pragma config WRT1 = OFF
#pragma config WRT2 = OFF
#pragma config WRTB = OFF //PROTECCI?N DE ESCRITURA PARA EL BLOCK DE BOOT
#pragma config WRTC = OFF //Configuration Register Write Protection bit,disable
#pragma config WRTD = OFF //Data EEPROM Write Protection bit,is not write protected
#pragma config EBTR0 = OFF //000800-001FFFh
#pragma config EBTR1 = OFF //Boot Block Table Read Protection bit,disable between
#pragma config EBTRB = OFF //000000-0007FFh and 002000-003FFFh
#pragma config CCP2MX = OFF
#pragma config DEBUG = ON //ENABLE FOR PICKIT 3
//DISABBLE THE DEBUG OPTION WHEN You're going to do the proper deployment.
#ifdef __cplusplus
}
#endif
#endif /* FUSES_H */
1/15/2014 FWD: Security Risks of Embedded Systems
| Microcontrollers and Chips are the main problem to update to the proper firmware |
It's not unlike what happened in the mid-1990s, when the insecurity of personal computers was reaching crisis levels. Software and operating systems were riddled with security vulnerabilities, and there was no good way to patch them. Companies were trying to keep vulnerabilities secret, and not releasing security updates quickly. And when updates were released, it was hard -- if not impossible -- to get users to install them. This has changed over the past twenty years, due to a combination of full disclosure -- publishing vulnerabilities to force companies to issue patches quicker -- and automatic updates: automating the process of installing updates on users' computers. The results aren't perfect, but they're much better than ever before.
But this time the problem is much worse, because the world is different: All of these devices are connected to the Internet. The computers in our routers and modems are much more powerful than the PCs of the mid-1990s, and the Internet of Things will put computers into all sorts of consumer devices. The industries producing these devices are even less capable of fixing the problem than the PC and software industries were.
If we don't solve this soon, we're in for a security disaster as hackers figure out that it's easier to hack routers than computers. At a recent Def Con, a researcher looked at thirty home routers and broke into half of them -- including some of the most popular and common brands.
To understand the problem, you need to understand the embedded systems market.
Typically, these systems are powered by specialized computer chips made by companies such as Broadcom, Qualcomm, and Marvell. These chips are cheap, and the profit margins slim. Aside from price, the way the manufacturers differentiate themselves from each other is by features and bandwidth. They typically put a version of the Linux operating system onto the chips, as well as a bunch of other open-source and proprietary components and drivers. They do as little engineering as possible before shipping, and there's little incentive to update their "board support package" until absolutely necessary.
The system manufacturers -- usually original device manufacturers (ODMs) who often don't get their brand name on the finished product -- choose a chip based on price and features, and then build a router, server, or whatever. They don't do a lot of engineering, either. The brand-name company on the box may add a user interface and maybe some new features, make sure everything works, and they're done, too.
The problem with this process is that no one entity has any incentive, expertise, or even ability to patch the software once it's shipped. The chip manufacturer is busy shipping the next version of the chip, and the ODM is busy upgrading its product to work with this next chip. Maintaining the older chips and products just isn't a priority.
And the software is old, even when the device is new. For example, one survey of common home routers found that the software components were four to five years older than the device. The minimum age of the Linux operating system was four years. The minimum age of the Samba file system software: six years. They may have had all the security patches applied, but most likely not. No one has that job. Some of the components are so old that they're no longer being patched. This patching is especially important because security vulnerabilities are found "more easily" as systems age.
To make matters worse, it's often impossible to patch the software or upgrade the components to the latest version. Often, the complete source code isn't available. Yes, they'll have the source code to Linux and any other open-source components. But many of the device drivers and other components are just "binary blobs" -- no source code at all. That's the most pernicious part of the problem: No one can possibly patch code that's just binary.
Even when a patch is possible, it's rarely applied. Users usually have to manually download and install relevant patches. But since users never get alerted about security updates, and don't have the expertise to manually administer these devices, it doesn't happen. Sometimes the ISPs have the ability to remotely patch routers and modems, but this is also rare.
The result is hundreds of millions of devices that have been sitting on the Internet, unpatched and insecure, for the last five to ten years.
Hackers are starting to notice. Malware DNS Changer attacks home routers as well as computers. In Brazil, 4.5 million DSL routers were compromised for purposes of financial fraud. Last month, Symantec reported on a Linux worm that targets routers, cameras, and other embedded devices.
This is only the beginning. All it will take is some easy-to-use hacker tools for the script kiddies to get into the game.
And the Internet of Things will only make this problem worse, as the Internet -- as well as our homes and bodies -- becomes flooded with new embedded devices that will be equally poorly maintained and unpatchable. But routers and modems pose a particular problem, because they're: (1) between users and the Internet, so turning them off is increasingly not an option; (2) more powerful and more general in function than other embedded devices; (3) the one 24/7 computing device in the house, and are a natural place for lots of new features.
We were here before with personal computers, and we fixed the problem. But disclosing vulnerabilities in an effort to force vendors to fix the problem won't work the same way as with embedded systems. The last time, the problem was computers, ones mostly not connected to the Internet, and slow-spreading viruses. The scale is different today: more devices, more vulnerability, viruses spreading faster on the Internet, and less technical expertise on both the vendor and the user sides. Plus vulnerabilities that are impossible to patch.
Combine full function with lack of updates, add in a pernicious market dynamic that has inhibited updates and prevented anyone else from updating, and we have an incipient disaster in front of us. It's just a matter of when.
We simply have to fix this. We have to put pressure on embedded system vendors to design their systems better. We need open-source driver software -- no more binary blobs! -- so third-party vendors and ISPs can provide security tools and software updates for as long as the device is in use. We need automatic update mechanisms to ensure they get installed.
The economic incentives point to large ISPs as the driver for change. Whether they're to blame or not, the ISPs are the ones who get the service calls for crashes. They often have to send users new hardware because it's the only way to update a router or modem, and that can easily cost a year's worth of profit from that customer. This problem is only going to get worse, and more expensive. Paying the cost up front for better embedded systems is much cheaper than paying the costs of the resultant security disasters.
This essay originally appeared on Wired.com.
http://www.wired.com/opinion/2014/01/theres-no-good-way-to-patch-the-internet-of-things-and-thats-a-huge-problem/ or http://tinyurl.com/ngoxykw
Security vulnerabilities in routers:
https://www.defcon.org/images/defcon-18/dc-18-presentations/Heffner/DEFCON-18-Heffner-Routers.pdf or http://tinyurl.com/mycykl7
Security vulnerabilities of older systems:
http://www.acsac.org/2010/openconf/modules/request.php?module=oc_program&action=view.php&a=&id=69&type=2 or http://tinyurl.com/l57yph8
Embedded malware:
http://news.cnet.com/8301-10784_3-9970972-7.html
http://nakedsecurity.sophos.com/2012/10/01/hacked-routers-brazil-vb2012/ or http://tinyurl.com/8js9jg2
http://www.symantec.com/connect/blogs/linux-worm-targeting-hidden-devices or http://tinyurl.com/ncwl6rr
http://arstechnica.com/security/2013/11/new-linux-worm-targets-routers-cameras-internet-of-things-devices/ or http://tinyurl.com/mcv73mj
Two essays that debunk the "NSA surveillance could have stopped 9/11" myth:
http://www.cnn.com/2013/12/30/opinion/bergen-nsa-surveillance-september-11/
http://www.newyorker.com/talk/comment/2014/01/13/140113taco_talk_wright
The changing cost of surveillance:
http://ashkansoltani.org/2014/01/09/the-cost-of-surveillance/
http://www.yalelawjournal.org/the-yale-law-journal-pocket-part/constitutional-law/tiny-constables-and-the-cost-of-surveillance:-making-cents-out-of-united-states-v.-jones
Source :
CRYPTO-GRAM, January 15, 2014
Subscribe to:
Comments (Atom)





